Miravia Open Platform
Arise - Security Review Process
How to Apply for Data Unmask
Login to https://open.lazada.com/ > APP Console > Click Manage under Action > Sensitive Data Privilege > Apply Unmask

A message will be pop up to prepare you with the the overall security process information. Please read the information carefully. Please note that any false information provided in the answer will lead to permanent denial of access to customer sensitive data.

Please acknowledge that you have read through the information and agree to provide accurate app information. The page is then automatically redirected to the DataMoat Console. It is mandatory to complete the Datamoat security review process for requested APPKEY within 2 weeks after that any request "In Progress" status will be closed by the system and then need to request for the unmask data again from step 1.
Security Review Process Steps
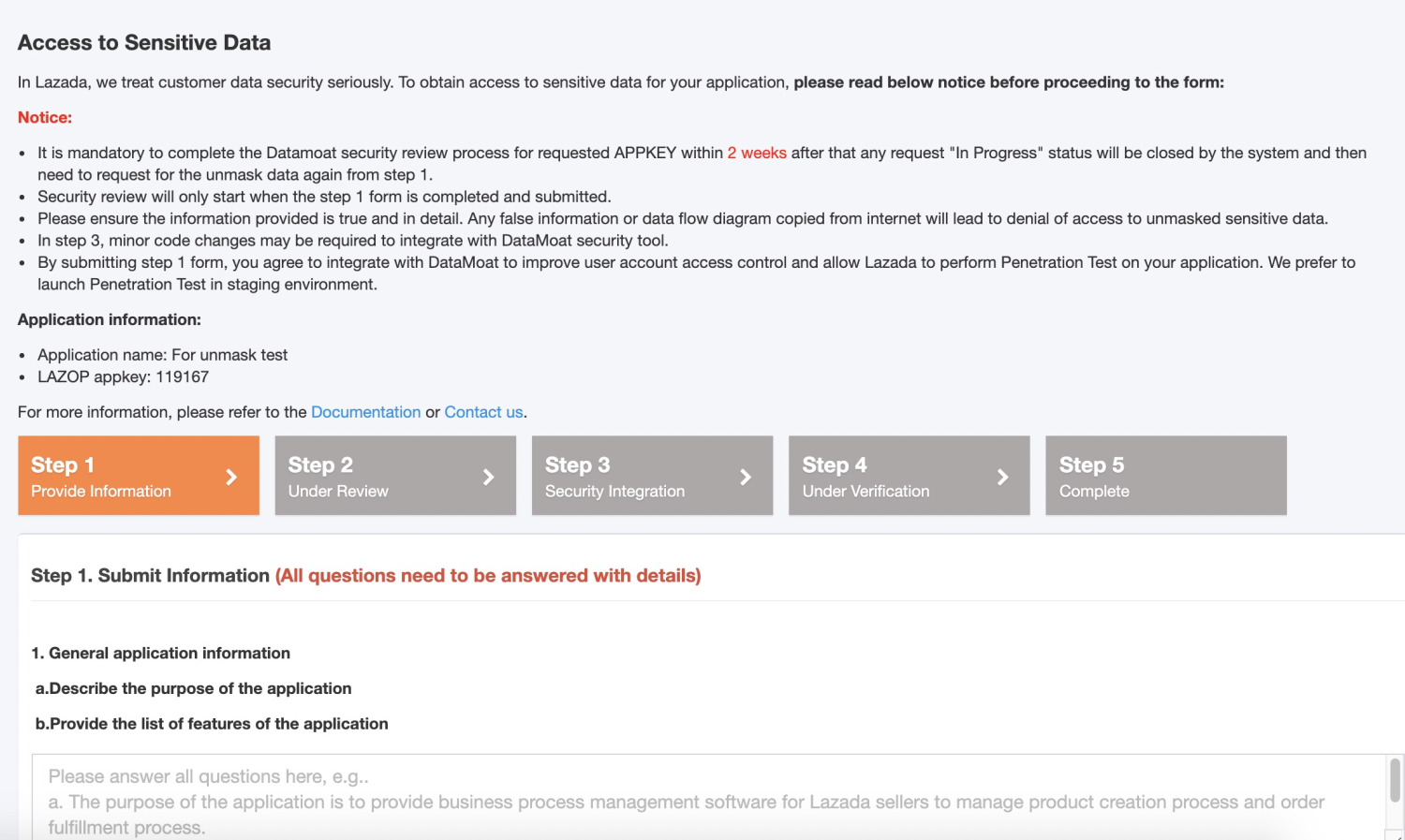
Step 1 Provide App Information
Once you are in the DataMoat Console, please fill in and submit all the information about your application architecture.
- Please ensure your application is using https over public network for user access.
- Please ensure your application as independent app level user access control to ensure only authenticated and authorized user can access to the application function.
- Please refer to Data Flow Diagram document if you are not sure what to upload.
- Do not copy any data flow diagram online or from the documentation (you application will be rejected immediately).
- Ensure the Data flow diagram clearly shows how the sensitive data is handled in your environment when data is in transit, in use, and at rest.
If you have any additional questions to clarify when you fill in the the step 1 form, please leave the question in the 1st textbox in the form and click "submit" button. We will provide feedback and review your answers once the step 1 form is submitted.
Step 2 LazOP Review Application Information
LazOp team will review the submitted application information. The status should now change to Under Review.
- If all security requirements are fulfilled, the request will be moved to step 3 within 1-5 days. There is no action required from ISV side.
- If any of the security requirements is not met, the request will be rejected with rejection feedback. Please review the feedback and make necessary changes to the application before submitting the step 1 form again.
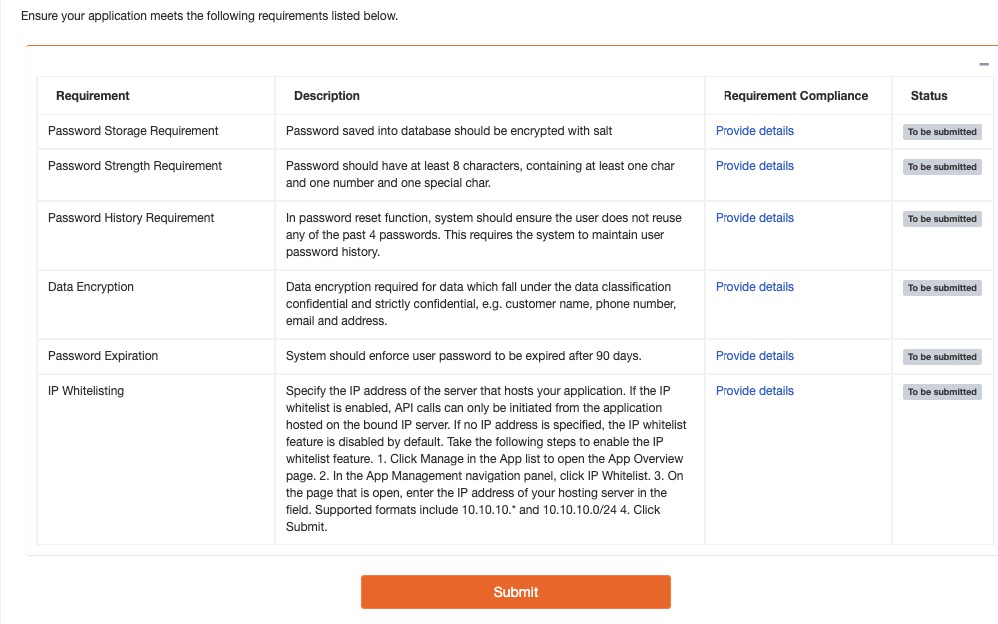
Step 3.1 Security Requirements
The purpose of this step is to ensure the sensitive information is properly protected. There are two types of sensitive data:
- For password: to verify that password is hashed with salt, complexity requirements are imposed, password history is maintained, and password expiration date is set. Please use strong hash algorithm such as SHA2 or slow hash functions such as Argon2, PBKDF2, bcrypt or Scrypt . Please note that MD5 and SHA1 are weak and broke.
- For customer sensitive personal information : sensitive data should be encrypted with at application level before saving into the database. Please use strong encryption algorithm with adequate key length such as AES with at lease 128 bits key length and in GCM mode.
LazOp team will review the submitted information:
- If all security requirements are fulfilled, the request will be moved to step 3.2 within 1-5 days.
- If any of the security requirements is not met, the request will be rejected with rejection feedback. Please review the feedback and make necessary changes to the application before submitting the step 3.1 form again.
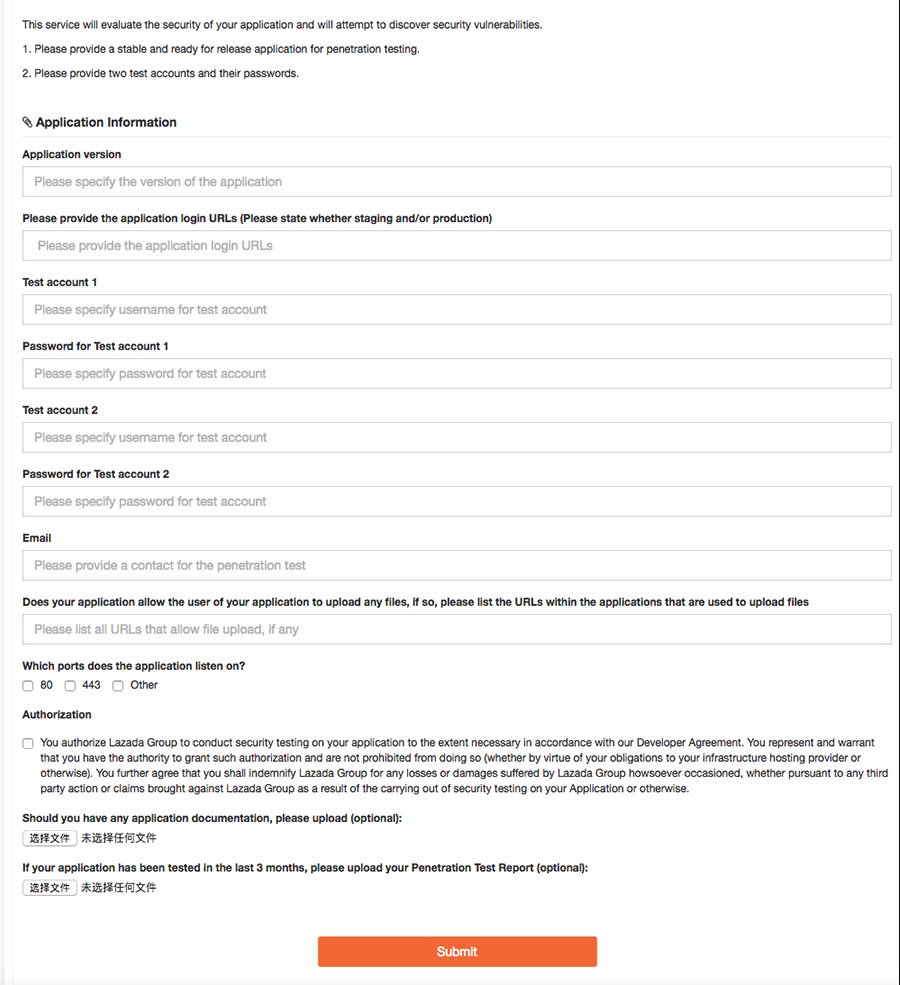
Step 3.2 Penetration Test
Please fill in the PenTest information required:
- We strongly recommend to carry out the penetration test on your staging environment. Please also have your data fully backed up before the test.
- Please use https and make sure the URL is accessible. We will reject applications with invalid test URL.
- Please provide 2 test accounts from different user roles or user group. For example,
- Provide 1 test account from normal user role and 1 test account from admin role.
- Provide 1 test account from seller A and 1 test account form seller B.
- Please read the "Authorization" notice carefully and authorize Lazada carrying out of security testing on the test application URL with the test credentials.
- If your application has been tested within past 3 months by a third party tester, please attach the test report in the form. We will verify the test report if the test scope and methodology fulfills our requirements and pass the Pentest step based on the report.
- Please click here for our Penetration Test methodology details.
Initial PenTest Scheduling:
- Test is scheduled based on first come first serve basis.
- Initial test will be completed in 1 day to 3 weeks.
- If there is any vulnerability reported, this step will be marked as "Not Pass" with feedback provided in the "Problems and fix suggestions" section.
- Vulnerabilities will be notified by the Message Center as well as an email , and details are listed under Vulnerability Management on DataMoat Console. Login to https://open.lazada.com/ > APP Console > DataMoat > Security Operation > Vulnerability Management (or click here )
- Please read trough the vulnerabilities and recommendation. Once all the vulnerabilities are fixed, please submit the updated test information again. This step will be repeated until all the vulnerabilities reported are cleared
PenTest Re-test Scheduling:
- Re-test typically takes 1-5 working days for the first 2 rounds of retest.
- From the 3rd rounds of re-test onward, 1 month additional delay for re-test will be added to start retest date.
- Please raise a LazOP ticket under "security testing" category for technical support if you need any help from fixing the vulnerabilities.
Step 4 Under Verification
LazOp team will review the security review process at this step. The request will be approved within 1-2 working days. Not action required from you in this step.

