文档中心
> Lazada Open Platform
Lazada Open Platform
- Overview
-
Quick Start Guide
- Getting started
- Registration and Authorization process for newly registered ISVs
- Become a developer
- Register an application
- Retrieve App Key and App Secret
- Request API permission
- Start development
- Seller authorization introduction
- Configure seller authorization
- The Process of Creating Test Order
- Redmart api interface guide
-
API Best Practice
- OMS integrate with Lazada
- Product operation
- Order operation
- Seller Notification
- Financial inquiry
- Instant Messaging
- Lazada large package receiving "ISV_ERP" interface
- Sponsored Solutions
- Reverse order
- Lazada Marketplace Ease Mode API Reference - 中文
- Lazada Marketplace Ease Mode API Reference - EN
- Global Plus Product Upgrade
-
Push Mechanism(WebHook) Application
- Push API (Webhook)
- Webhook - CN
-
Webhook APIs
- Webhook API Trade Order Notifications
- Webhook API Product Quality Control Notification
- Webhook API Product Update Notificaton
- Webhook API Shallow Stock Notification
- Webhook API Short Video State Update Notification
- Webhook API Authorization Token Expiration Alert
- Webhook API Product Category Update Notification
- Webhook API Seller Status Update Notification
- Webhook API Fulfillment Order Update Notification
- Webhook API Reverse Order
- Webhook API Promotion
- Webhook API Product Review Notification
- Webhook API JIT PO Status Update Notification
- Webhook API IM Send Message Notifications
- Webhook API IM Session Update Notifications
- API Reference
- Advanced Tasks
- Developer's Guide
-
Security Center
- Security Measures
- Lazada Partner Application Security Guidelines
- Security Review Process
- Terms and Agreement
- FAQ
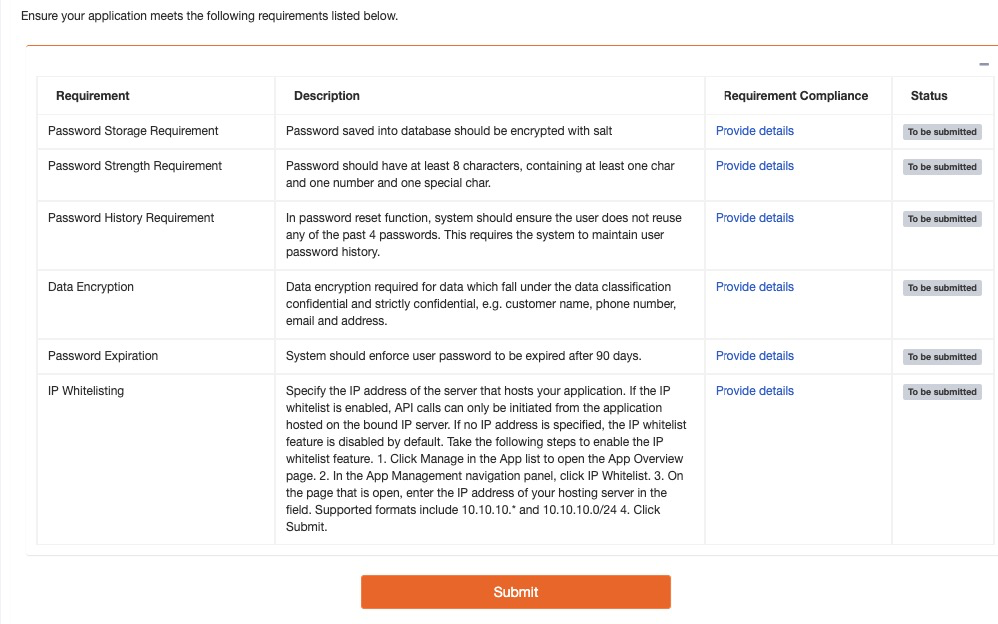
Step 3.1 Security Requirements
更新时间:2022/04/15
访问次数:2444
The purpose of this step is to ensure the sensitive information is properly protected. There are two types of sensitive data:
- For password: to verify that password is hashed with salt, complexity requirements are imposed, password history is maintained, and password expiration date is set. Please use strong hash algorithm such as SHA2 or slow hash functions such as Argon2, PBKDF2, bcrypt or Scrypt . Please note that MD5 and SHA1 are weak and broke.
- For customer sensitive personal information : sensitive data should be encrypted with at application level before saving into the database. Please use strong encryption algorithm with adequate key length such as AES with at lease 128 bits key length and in GCM mode.
LazOp team will review the submitted information:
- If all security requirements are fulfilled, the request will be moved to step 3.2 within 1-5 days.
- If any of the security requirements is not met, the request will be rejected with rejection feedback. Please review the feedback and make necessary changes to the application before submitting the step 3.1 form again.