Lazada Open Platform
Access to Sensitive Data
How to access Sensitive Data - unmasking Request
You need to go through the following procedure to request access to the sensitive data which are masked. This page describes the steps to unmask the business data which are categorized as sensitive according to the Data Classification Policy.
Security process for unmasking the sensitive data consists of the following steps:
-
Application Architecture Information Form
-
Port requirement
-
Data Flow Diagram
-
Hosting environment
-
Other relevant information
-
-
DataMoat Integration
-
Security requirements
-
Penetration test
-
-
Vulnerability assessment
-
Verification
Procedure
Apply for Unmasking Data
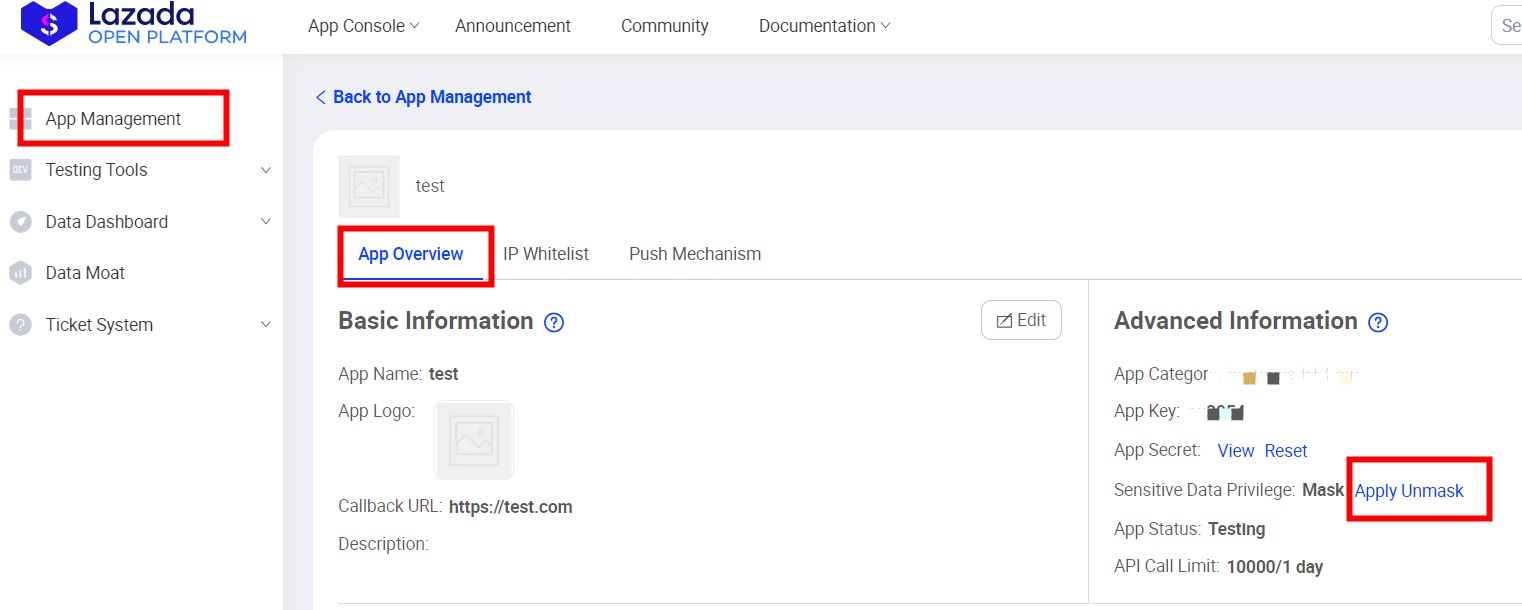
Login to https://open.lazada.com/ > APP Console > Click Manage under Action > Sensitive Data Privilege > Apply Unmask
- The page is automatically redirected to the Data Registration App.
- It is mandatory to complete the Datamoat security review process for requested APPKEY within 2 weeks after that any request "In Progress" status will be closed by the system and then need to request for the unmask data again from step 1.
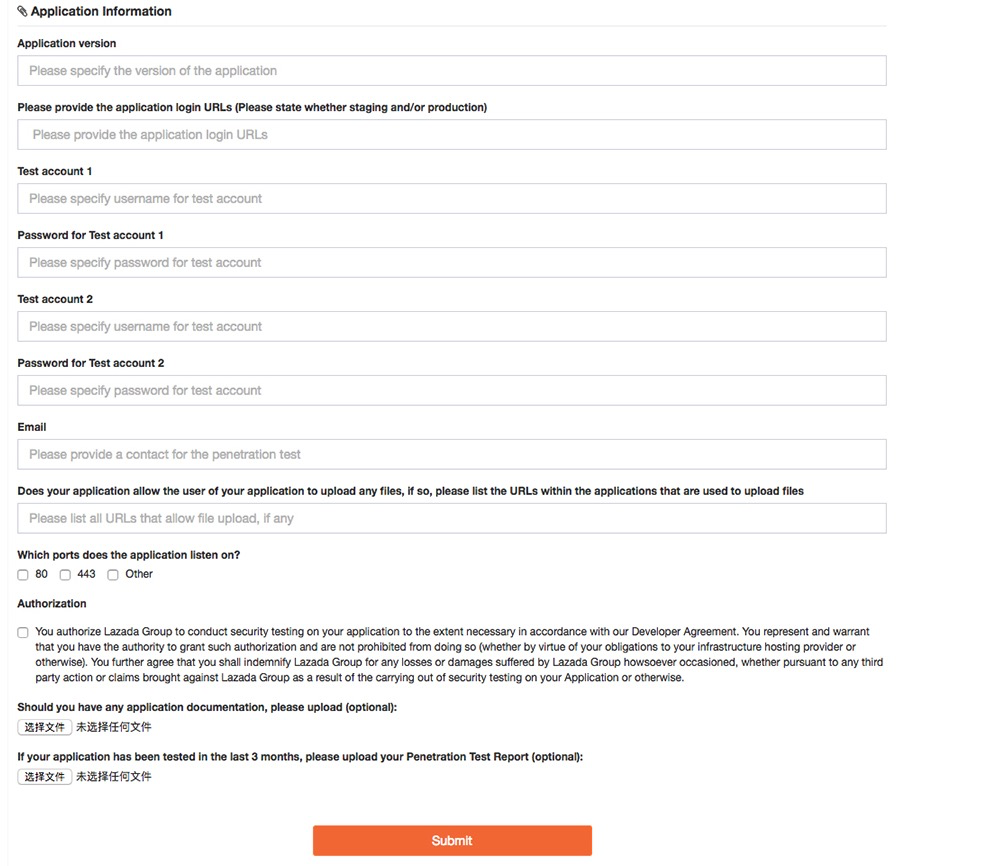
Step 1. Fill in your Application Architecture Information Form
Once you are in the DataMoat Console, please fill in and submit the information about your application architecture.
- Please use https and make sure the URL is accessible, otherwise there is a possibility that your application is rejected.
- Please refer to Data Flow Diagram document if you are not sure what to upload

Step 2. Your application is being reviewed (No action required)
The status should now change to Under Review . Lazada will review the application form you have submitted in the previous step.
- We are pleased to receive a large amount of interest! However, please expect a delay in our response although we are trying our best to reach out to you as soon as possible. Should you have questions, please raise a ticket to us from Contact Us .
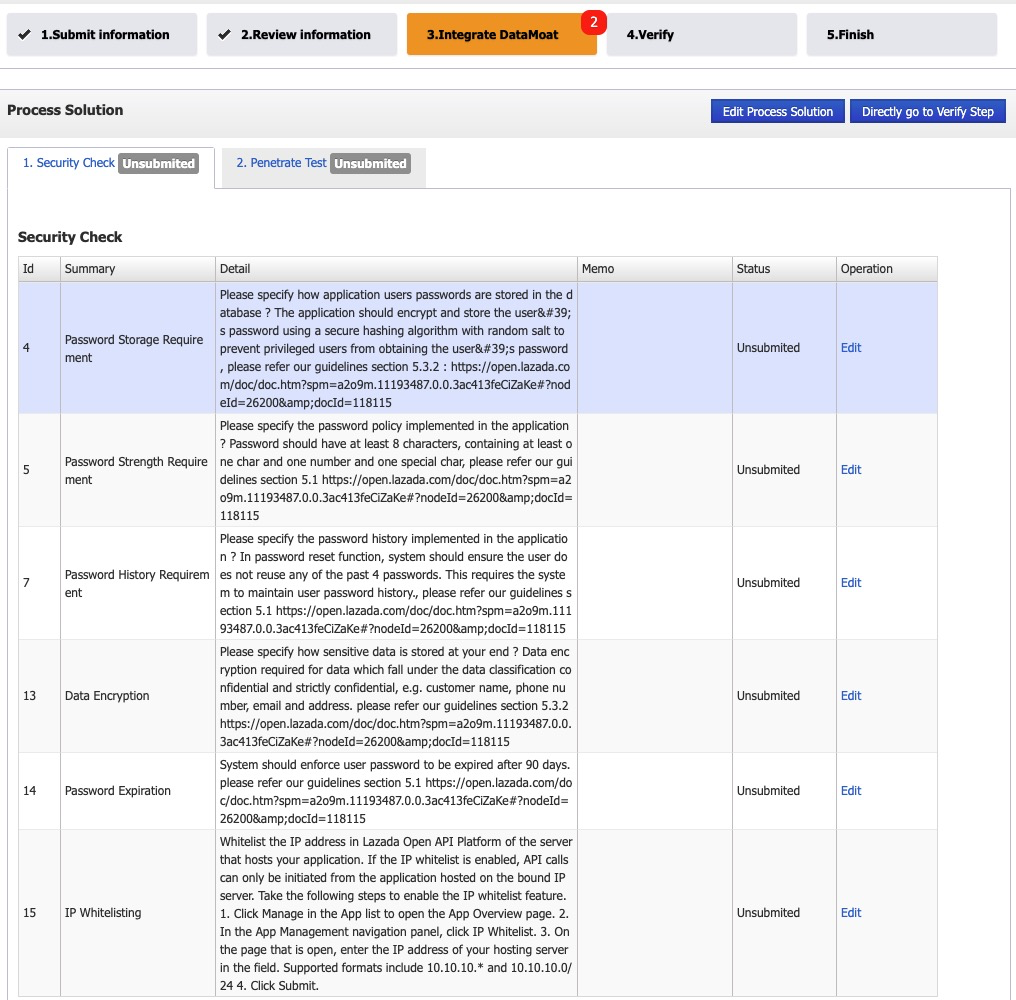
Step 3. DataMoat Integration
The type of security controls depend on Step 2 review result, however, typically this step consists of :
- Security Requirements (password)
- Penetration Test
Step 3.1. Security Requirements
This is the list of our security requirement.
- Please state how your application is complying with each item by clicking Provide details under Requirement Compliance
Step 3.2. Penetration Test
Please fill in the information required for penetration testing.
- Please use https and make sure the URL is accessible, otherwise there is a possibility that your application is rejected.
- We strongly recommend to carry out the penetration test on your staging environment. Please also have your data fully backed up before the test.
- Once the penetration test is scheduled, an email and/or ticket notification will be sent to your registered email address or to the message center on your LAZOP console. Such notification will be sent at least 2 days prior to the test schedule. Should you have any conerns, please reply directly to our email or raise a ticket via Contact US under Security Testing category.
- Vulnerabilities that are assessed will be notified by the Message Center as well as an email , and details are listed under Vulnerability Management on DataMoat Console.
Login to https://open.lazada.com/ > APP Console > DataMoat > Security Operation > Vulnerability Management (or click here )
- Please click here for our Penetration Test methodology details.
- This step will be repeated until all the vulnerabilities assessed are cleared
- Security Test typically takes up to 5 working days from the day Lazada receives adequate information to perform the test
Step 4. Final Verification (No action required)
You will be notified once verification is complete via an email or message center on LAZOP console.
Step 5. Complete
The sensitive data is now unmasked.
Any Questions?
Please raise a ticket from Contact Us under Security Review question category.